Introduction
Network layers serve as a fundamental framework that enables the seamless flow of data and communication across networks. Network layers, also known as protocol layers, play a crucial role in modern networking by organizing the communication process into manageable and structured components. Each layer has a specific set of responsibilities and protocols, contributing to the overall efficiency and reliability of network operations.
By dividing the complex task of network communication into separate layers, it becomes easier to troubleshoot and maintain networks. Network layers provide a modular approach, allowing engineers to focus on specific aspects without disrupting the entire system. This modular design enhances scalability and promotes interoperability between different network devices and technologies.
Furthermore, network layers facilitate the implementation of advanced features and services. By layering protocols, networks can support functionalities such as encryption, error detection and correction, congestion control, quality of service (QoS) management, and routing algorithms. These capabilities enable the development of robust and secure network infrastructures.
Overview of the Article and Its Objective
This blog post on CSITechLK will give readers insights into the benefits of comprehending network layers, including enhanced troubleshooting abilities, improved network design, and the ability to leverage advanced networking features. Whether you are a seasoned networking professional or an enthusiastic learner, this article will equip you with the knowledge to navigate complex network layers confidently.
Importance of Understanding Network Layers
Understanding network layers is vital for professionals and enthusiasts involved in networking. We will be discussing the following points.
1. Efficient Troubleshooting: Network layers allow engineers to pinpoint and resolve issues by isolating problems within specific layers. This targeted troubleshooting approach saves time and resources, ensuring faster network restoration.
2. Optimized Network Design: Knowledge of network layers empowers professionals to design scalable and efficient networks. By considering the unique characteristics and requirements of each layer, engineers can create robust architectures that align with organizational needs.
3. Enhanced Collaboration: Professionals who grasp the concept of network layers can effectively communicate and collaborate with peers. Using a common language and understanding of network layers facilitates seamless cooperation in network planning, implementation, and troubleshooting.
4. Career Advancement: A solid grasp of network layers is highly sought after in the job market. Employers value professionals who possess a deep understanding of networking fundamentals, making it a valuable skill for career growth and advancement.
Comprehending network layers is indispensable in the world of modern networking. This article of CSITechLK will be a valuable resource, providing the knowledge and insights needed to navigate and optimize network infrastructures effectively. Whether you are a seasoned professional or an enthusiastic learner, embracing the intricacies of network layers will undoubtedly unlock new possibilities in your networking journey.
Understanding Network Layers
Network layers provide a structured framework for organizing and managing the flow of data. In this article section, we will explore the concept of network layers, delve into the OSI model, and discuss the TCP/IP model's relationship with network layers.
Definition of Network Layers
Network layers can be thought of as distinct levels or tiers within a network architecture. Each layer has specific responsibilities and performs designated functions. These layers work together to ensure efficient and reliable communication between devices and systems connected to the network layers.
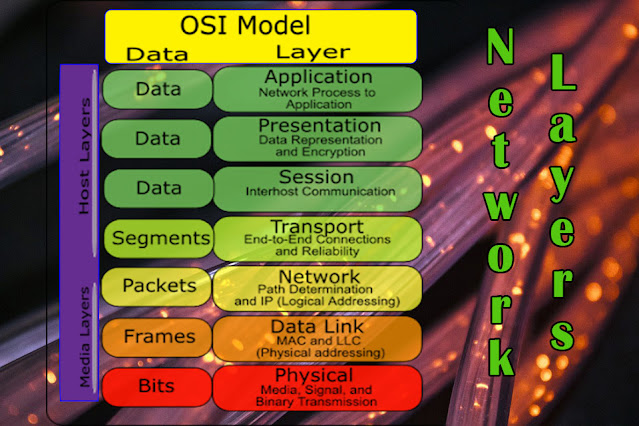
Overview of the OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes network layers communication. It consists of seven layers, each responsible for a specific aspect of data transmission.
The significance of the OSI model lies in its ability to facilitate interoperability between different network technologies. By dividing the communication process into discrete layers, it allows for standardized protocols and enables the seamless exchange of data across diverse networks.
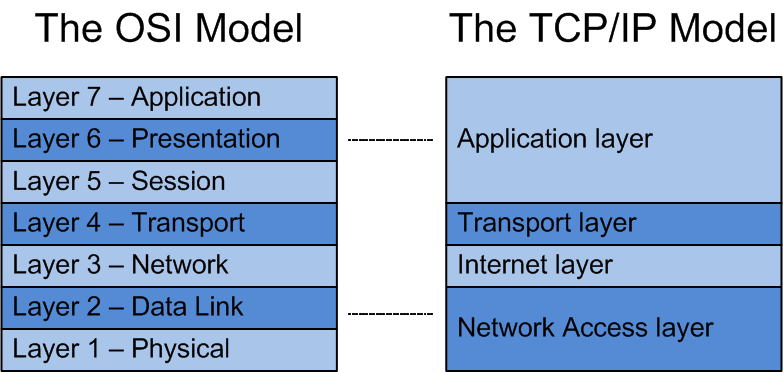
Explanation of the TCP/IP Model and its Relation to Network Layers
The TCP/IP (Transmission Control Protocol/Internet Protocol) model is another widely used network protocol suite. It predates the OSI model and has become the foundation of the modern internet. While the TCP/IP model doesn't strictly adhere to the layer-based approach like the OSI model, it aligns with the concept of network layers.
In the TCP/IP model, the layers can be roughly mapped to their counterparts in the OSI model. The Network Interface layer corresponds to the Physical and Data Link layers, the Internet layer aligns with the Network layer, the Transport layer remains the same, and the Application layer encompasses the Session, Presentation, and Application layers of the OSI model.
The TCP/IP model's relationship with network layers underscores the importance of modular and hierarchical design in networking. It allows for flexible implementation, scalability, and interoperability across various network environments.
In conclusion, understanding network layers, including the OSI model and the TCP/IP model, is crucial for comprehending how data flows and is managed within a network. These models provide a structured framework that aids in efficient communication and ensures the smooth
Layer 1: Physical Layer
The Physical Layer serves as the foundation of computer network communication. It focuses on the actual transmission and reception of raw data bits over a physical medium. In this section, we will explore the definition, functions, hardware components, protocols, and associated devices and technologies of the Physical Layer.
Definition and Functions of the Physical Layer
The Physical Layer is responsible for establishing and maintaining the physical connection between network devices. This layer's primary function is to send and receive data by converting it to electrical, optical, or radio signals suitable for transmission through a network medium.
Hardware Components and Protocols Used in the Physical Layer
The Physical Layer utilizes various hardware components and protocols to facilitate data transmission. These include:
1. Network Cables: Ethernet cables, such as Cat5e or Cat6, are commonly used for wired network connections. Fiber optic cables offer higher bandwidth and longer distance capabilities.
2. Network Interfaces: Network interface cards (NICs) or Ethernet adapters are the physical interfaces that connect devices to the network. They handle the conversion of data between digital signals used by computers and the appropriate electrical or optical signals used for transmission.
3. Connectors and Jacks: RJ-45 connectors and jacks are commonly used with Ethernet cables, while fiber optic connectors, such as LC or SC connectors, are used with fiber optic cables.
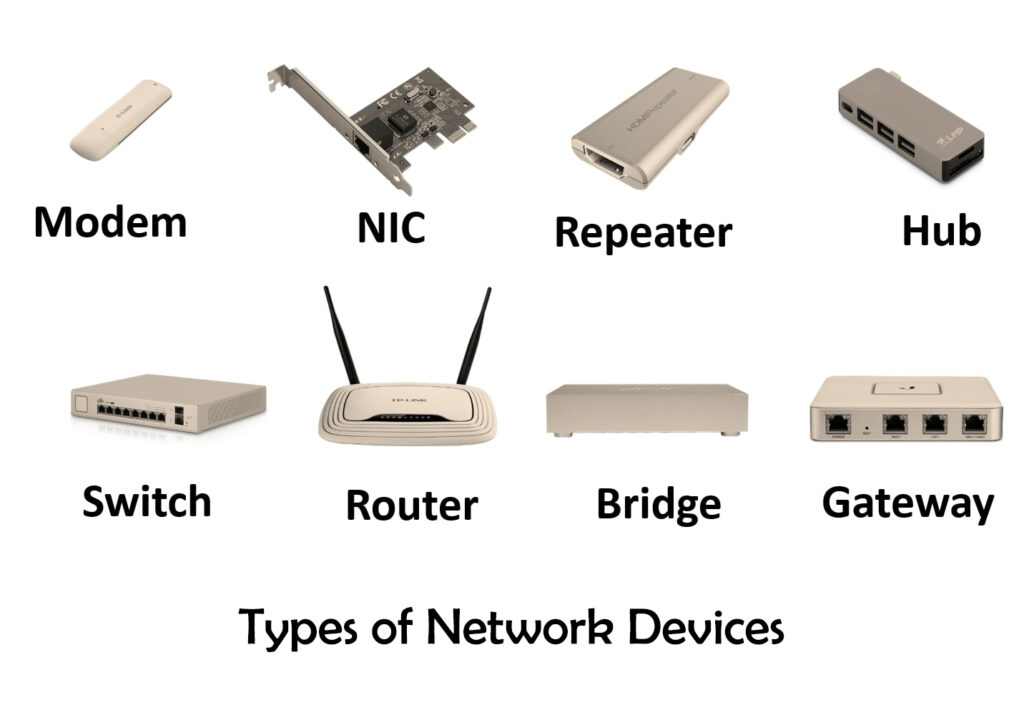
4. Repeaters and Hubs: These devices amplify and regenerate signals to extend the reach of the network layers over longer distances.
Examples of Devices and Technologies Associated with the Physical Layer
Several devices and technologies are closely associated with the Physical Layer. Some notable examples include:
1. Ethernet Switches: These network devices operate at the Data Link Layer but have a physical component responsible for connecting devices at the Physical Layer.
2. Modems: Modems convert digital signals from computers into analog signals for transmission over telephone lines, cable lines, or wireless networks.
3. Wireless Access Points: These devices enable wireless connectivity by transmitting and receiving signals over the air.
4. Network Hubs: While less common today, network hubs were once used to connect multiple devices within a local area network, operating at the Physical Layer.
The Physical Layer plays a crucial role in network layers communication by ensuring the transmission of raw data bits over the network medium. By understanding its functions, hardware components, protocols, and associated devices and technologies, we gain a deeper appreciation of the underlying infrastructure that enables modern network connectivity.
Layer 2: Data Link Layer
The Data Link Layer is an essential component of computer networks, responsible for the reliable transfer of data between adjacent network nodes. In this section, we will explore the definition and functions of the Data Link Layer, delve into the concept of MAC addresses, discuss data framing and error detection, and examine some commonly used devices and protocols associated with this layer.
Definition and Functions of the Data Link Layer
The Data Link Layer provides a reliable link between two directly connected network nodes, ensuring error-free data transmission. Its primary functions include:
MAC Addresses and Their Role
MAC addresses, also known as Media Access Control addresses, are unique identifiers assigned to network interface cards (NICs) at the Data Link Layer. They play a vital role in identifying devices within a local area network (LAN). MAC addresses consist of a 48-bit binary number. The representation of this number is in hexadecimal format. They enable the Data Link Layer to correctly route data frames to the intended destination.
Data Framing and Error Detection in the Data Link Layer
Data framing is a key process in the Data Link Layer that involves encapsulating data into frames for transmission. Each frame contains a header, data payload, and a trailer. The header and trailer include control information, such as source and destination MAC addresses, sequence numbers, and error detection codes.
Error detection mechanisms, such as **Cyclic Redundancy Check (CRC)**, are employed to ensure data integrity at the Data Link Layer. CRC calculates a checksum based on the data contents and appends it to the frame. Upon reception, the receiving device performs a CRC calculation to check for errors. If a mismatch occurs, the frame is discarded and retransmission may be requested.
Examples of Devices and Protocols Used in the Data Link Layer
Several devices and protocols are commonly associated with the Data Link Layer. Here are some examples:
The Data Link Layer plays a crucial role in ensuring reliable data transmission between directly connected network nodes. By understanding its functions, the significance of MAC addresses, the process of data framing, and the protocols and devices associated with this layer, we gain insights into the underlying mechanisms that facilitate seamless communication within computer networks.
Layer 3: Network Layer
The Network Layer is a crucial component of computer networks, responsible for logical addressing, routing, and the efficient delivery of data packets across different networks. In this article section, we will delve into the definition and functions of the Network Layer, explore IP addresses, subnetting, and routing, discuss protocols like IPv4 and IPv6, and examine examples of devices and protocols utilized in this layer.
Definition and Functions of the Network Layer
The Network Layer facilitates end-to-end communication between hosts on different networks. Its primary functions include:
Logical Addressing: The Network Layer assigns logical addresses, such as IP addresses, to devices connected to the network. These addresses enable the identification and location of hosts, ensuring proper delivery of data packets.
Overview of IP Addresses, Subnetting, and Routing
IP Addresses: IP addresses are unique numerical identifiers assigned to devices on a network. IPv4 addresses, consisting of four sets of numbers, were widely used but are being replaced by IPv6 addresses, which provide a larger address space. IP addresses allow for proper addressing and routing of data packets.
Subnetting: This is a technique used to divide a large network into small manageable networks. It helps in optimizing network resources, improving security, and facilitating efficient routing by creating smaller broadcast domains.
Routing: Routing involves determining the best path for data packets to travel across multiple networks. Routers, key devices in the Network Layer, use routing tables and algorithms to make decisions based on factors like network congestion, link quality, and destination addresses.
Protocol explanations include IPv4, IPv6, and routing algorithms
Routing Algorithms: Few examples of routing protocols are RIP (Routing Information Protocol), OSPF (Open Shortest Path First), and BGP (Border Gateway Protocol). These algorithms help routers make intelligent decisions about the best paths for data packets based on factors like cost, speed, and network layers topology.
Examples of Devices and Protocols Used in the Network Layer
ICMP: The Internet Control Message Protocol (ICMP) is another protocol within the Network Layer. It is in charge of administration, network diagnostics, and fault-reporting tasks. It makes use of a 128-bit addressing method, allowing for a far greater number of unique addresses to handle the expanding number of internet-connected devices.
Network Layer Switches: These devices, also known as Layer 3 switches, combine the capabilities of routers and switches, performing routing functions at higher speeds within local area networks.
In conclusion, the Network Layer plays a critical role in ensuring efficient communication between networks. Understanding its functions, IP addressing, subnetting, routing protocols, and the devices and protocols associated with this layer helps in building and maintaining robust and scalable networks.
Layer 4: Transport Layer
The Transport Layer is a vital component of computer networks, responsible for the reliable and orderly delivery of data between host systems. In this article section, we will explore the definition and functions of the Transport Layer, delve into transport protocols like TCP and UDP, discuss the role of port numbers, and examine examples of devices and protocols used in this layer.
Definition and Functions of the Transport Layer
The Transport Layer ensures the efficient and error-free delivery of data between applications running on different hosts. Its primary functions include:
Overview of Transport Protocols such as TCP and UDP
TCP (Transmission Control Protocol): TCP is a connection-oriented transport protocol that guarantees the reliable delivery of data. It provides features such as error detection, retransmission of lost segments, and sequencing of received data. TCP is commonly used for applications that require error-free and ordered delivery, such as web browsing, file transfer, and email.
UDP (User Datagram Protocol): UDP is a connectionless transport protocol that operates with minimal overhead. Unlike TCP, it does not provide reliability mechanisms such as error recovery or ordering of data. UDP is suitable for applications that prioritize speed and efficiency over error-free delivery, such as real-time streaming, online gaming, and DNS (Domain Name System) resolution.
Explanation of Port Numbers and Their Role in the Transport Layer
Port numbers are unique identifiers assigned to different applications or services running on a host. They help the Transport Layer identify the specific application to which incoming data should be delivered. Some key points about port numbers include:
Examples of Devices and Protocols Used in the Transport Layer
The Transport Layer plays a crucial role in ensuring reliable and efficient data delivery between applications. Understanding its functions, transport protocols like TCP and UDP, the significance of port numbers, and the devices and protocols associated with this layer is essential for building robust and scalable network architectures.
Layer 5: Session Layer
The Session Layer, the fifth layer of the OSI model, is responsible for establishing, managing, and terminating sessions between applications. In this article section, we will explore the definition and functions of the Session Layer, discuss session establishment, maintenance, and termination, provide an overview of protocols used in this layer, and highlight examples of devices and technologies associated with it.
Definition and Functions of the Session Layer
The Session Layer enables communication and coordination between different applications running on networked devices. Its primary functions include:
Session Establishment: During session establishment, the Session Layer handles the authentication and authorization process, ensuring that the participating applications are authorized to communicate with each other. It establishes the necessary connections and initializes parameters for the session.
Session Maintenance: Throughout the session, the Session Layer manages the synchronization of data flow, maintains the session state, and performs error recovery mechanisms. It also handles session timeout and handles issues related to session interruptions.
Session Termination: When the communication between applications is complete, the Session Layer initiates the termination process, ensuring that all resources allocated to the session are properly released and made available for future sessions.
Overview of Protocols Used in the Session Layer
NetBIOS (Network Basic Input/Output System): NetBIOS is a session layer protocol that provides services for naming, session establishment, and session maintenance in a local area network (LAN) environment.
Examples of Devices and Technologies Associated with the Session Layer
Gateways: Gateways, which operate at multiple layers of the OSI model, including the Session Layer, provide interconnectivity between networks with different protocols, allowing for seamless communication between applications.
The Session Layer plays a vital role in establishing, maintaining, and terminating sessions between applications. Understanding its functions, session establishment, maintenance, and termination processes, the protocols used in this layer, and the devices and technologies associated with it help in better network design.
Layer 6: Presentation Layer
The Presentation Layer, the sixth layer of the OSI model, focuses on the presentation and transformation of data to ensure compatibility between different systems. In this article section, we will explore the definition and functions of the Presentation Layer. We will discuss data encryption, compression, and format conversion, provide an overview of protocols and technologies used in this layer, and highlight examples of devices and applications associated with it.
Definition and Functions of the Presentation Layer
The Presentation Layer is responsible for formatting and presenting data in a manner that can be understood by the receiving application. Its primary functions include:
Data Format Conversion: The Presentation Layer handles the conversion of data formats such as text, images, audio, and video between different systems. It ensures that the receiving application can properly interpret and process the data.
Overview of Protocols and Technologies Used in the Presentation Layer
Examples of Devices and Applications Associated with the Presentation Layer
Graphics Cards: Graphics cards, commonly used in computers and gaming consoles, handle the processing and presentation of graphical data, ensuring smooth and visually appealing experiences.
Media Players: Media players, such as VLC and Windows Media Player, operate in the Presentation Layer to decode and render audio and video files, providing a seamless playback experience.
In conclusion, the Presentation Layer plays a crucial role in formatting, encrypting, compressing, and converting data to facilitate effective communication between different systems. Understanding its functions, data encryption, compression, and format conversion processes, the protocols and technologies used in this layer, and the devices and applications associated with it help in building robust and interoperable network architectures.
Layer 7: Application Layer
The Application Layer, the topmost layer of the OSI model, is responsible for providing network services and interfaces to end-users and applications. In this article section, we will explore the definition and functions of the Application Layer, discuss application protocols and their role, explain common applications and services in this layer, and provide examples of devices and technologies associated with it.
Definition and Functions of the Application Layer
The Application Layer serves as the interface between the network and the user, enabling communication and interaction with various applications.
Application Services: The Application Layer provides a wide range of services. Some of those are email, file transfer, web browsing, remote access, and collaboration tools.
Overview of Application Protocols and Their Role
HTTP (Hypertext Transfer Protocol): HTTP is a widely used protocol in the Application Layer, enabling the retrieval and display of web pages. It facilitates communication between web browsers and web servers, delivering web content to users.
Explanation of Common Applications and Services in the Application Layer
Web Browsers: All internet browsers, Safari, Firefox, and Chrome included, operate on the application layer. This is enabling users to access and browse websites, interact with web applications, and consume online content.
Email Clients: Email clients such as Microsoft Outlook, Gmail, and Apple Mail are applications that allow users to manage and send emails. They provide features like inbox organization, composing messages, and handling attachments.
Examples of Devices and Technologies Associated with the Application Layer
Web Servers: Web servers, such as Apache HTTP Server and Nginx, respond to client requests received through web browsers, delivering web pages and content over the network.
In conclusion, the Application Layer plays a vital role in providing services, interfaces, and communication capabilities to end-users and applications. Understanding its functions, application protocols, common applications, and services, as well as devices and technologies associated with it, helps
Importance of Network Layers in Communication
Network layers play a crucial role in enabling effective communication and ensuring reliable and efficient data transmission across networks. In this article section, we will explore the significance of network layers and how they contribute to seamless communication.
Discussing the Significance of Network Layers
Network layers serve as a structured approach to organizing the communication process.
Why they are important:
1. Modularity and Abstraction: Network layers provide a modular and hierarchical structure to network protocols. Each layer focuses on specific tasks and services, which allows for easier management, troubleshooting, and scalability. This modularity also promotes abstraction, meaning that higher-layer protocols can operate independently of lower-layer implementations.
2. Interoperability: Network layers facilitate interoperability between different systems and devices. By adhering to a standardized layering model, it becomes possible for devices from different manufacturers to communicate effectively. Each layer's protocols and services ensure that data can be transmitted and understood across diverse network architectures.
Explanation of How Network Layers Ensure Reliable and Efficient Data Transmission
The network layers play a vital role in ensuring the reliability and efficiency of data transmission.
How they achieved this:
1. Error Detection and Correction: Certain network layers, such as the Data Link layer, incorporate mechanisms for error detection and correction. These mechanisms help identify and recover from transmission errors, ensuring the integrity of data during transit.
2. Packet Routing and Forwarding: Network layers, particularly the Network layer, handle packet routing and forwarding. They determine the optimal path for data transmission, considering factors such as network congestion, traffic load, and the destination address. This routing process enables efficient and timely delivery of data packets.
3. Addressing and Segmentation: Network layers, like the Network and Transport layers, utilize addressing schemes to identify the source and destination of data. They also segment data into smaller, manageable units for transmission. This segmentation enables efficient use of network resources and helps prevent data loss in case of transmission failures.
By incorporating these features and functionalities, network layers ensure that data is transmitted reliably and efficiently across networks, regardless of their size or complexity.
In conclusion, network layers are of paramount importance in enabling effective communication. They provide a structured framework, ensure interoperability, and implement mechanisms for reliable and efficient data transmission. Understanding the significance of network layers is essential for building robust and scalable network architectures.
Conclusion
In this article, we have explored the significance of understanding network layers in networking architecture. By recapping the importance of network layers, highlighting their interdependence, and encouraging further exploration, we have emphasized the crucial role they play in ensuring efficient communication. Let's delve deeper into these points:
1. Structured Communication: Network layers provide a systematic approach to communication by dividing the process into manageable layers. Each layer focuses on well-defined specific tasks. Those tasks are addressing, routing, and data transmission, ensuring a well-organized and efficient flow of information.
2. Efficiency and Reliability: Network layers contribute to efficient and reliable data transmission. By assigning specific responsibilities to each layer, such as error detection and correction, congestion control, and data segmentation, they optimize the network's performance and enhance the overall reliability of communication.
3. Interoperability and Scalability: Network layers facilitate interoperability between different devices, protocols, and technologies. By adhering to standardized protocols, network components can seamlessly communicate with each other, promoting compatibility and scalability in network design.
Interdependence of Network Layers
Network layers are interconnected and depend on each other to ensure smooth communication. The layers work in tandem, with each layer building upon the services provided by the layer below it. This interdependence fosters a cohesive and coordinated approach to network communication.
For instance, the Physical Layer establishes the physical connection and transmits raw bit streams, which the Data Link Layer utilizes to organize the bits into data frames. The Network Layer then uses these data frames to route packets across networks, and the Transport Layer ensures the reliable delivery of packets between applications.
Encouraging Further Exploration
To deepen your understanding of network layers and their impact on networking architecture, consider the following steps:
1. Continual Learning: Stay updated with the latest developments in networking technologies, protocols, and best practices.
2. Hands-on Experience: Gain practical experience by working on networking projects, setting up networks, and troubleshooting common issues. The practical application enhances your understanding and problem-solving skills.
3. Certifications and Training: Consider pursuing professional certifications and training programs in networking and network architecture. Certifications provide recognition of your expertise and can open doors to new career opportunities.
4. Networking Communities: You can get connected with network engineers on social media and platforms like LinkedIn to communicate and share ideas and learn from the community.
By embracing a mindset of continual learning and exploration, you can become a proficient network professional with a deep understanding of network layers and their vital role in building efficient and robust communication networks.
In conclusion, understanding network layers is crucial for anyone involved in networking architecture. By recapping their importance, highlighting their interdependence, and encouraging further exploration, we have emphasized the significance of network layers in ensuring seamless and effective communication. Embrace the opportunities for learning and growth, and continue to evolve your skills in this dynamic field.
FAQs
Here are answers to some commonly asked questions about network layers:
1. What are the 7 layers in a network?
The 7 layers in a network are:
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
2. What are the 5 layers of the network layer?
The network layer consists of the following 5 layers:
- Network Layer
- Internet Layer
- Network Access Layer
- Link Layer
- Physical Layer
3. What is the network layer and its types?
The network layer is responsible for network addressing, routing, and packet forwarding. It ensures that data packets are delivered across multiple networks. The two main types of network layers are:
Connectionless network layer: This type of network layer delivers packets individually without establishing a dedicated connection.
Connection-oriented network layer: This type establishes a connection between source and destination before transmitting packets.
4. How does the OSI model define Layer 7?
According to the OSI model, Layer 7 is known as the Application Layer. It is responsible for providing network services and interfaces for applications to access network resources.
5. Which layer corresponds to the 7th layer in the OSI model?
The 7th layer in the OSI model corresponds to the Application Layer. It is responsible for providing network services to applications and end-users.
6. At which layer is Ethernet located?
Ethernet technology is operating at both the Data Link Layer (Layer 2) and the Physical Layer (Layer 1) of the OSI model Network Layers.
7. Is the network layer Layer 3 or Layer 7?
The network layer is Layer 3 in the OSI model. It is responsible for the logical addressing, routing, and forwarding of packets between networks.
8. What is the TCP 5-layer model?
The TCP 5-layer model is a simplified version of the TCP/IP protocol suite. It consists of the following layers:
- Network Interface Layer
- Internet Layer
- Transport Layer
- Application Layer
- Physical Layer
9. Is TCP Layer 3 or Layer 4?
TCP (Transmission Control Protocol) is a transport layer protocol, which makes it Layer 4 in the OSI model. It provides reliable, connection-oriented communication between applications.
10. Why are network layers important?
Network layers are important because they provide a structured and modular approach to network design and communication. They enable efficient data transmission, scalability, interoperability, and the ability to troubleshoot and manage networks effectively.
11. What are the 4 main types of computer networks?
The four main types of computer networks are:
- Local Area Network (LAN)
- Metropolitan Area Network (MAN)
- Wide Area Network (WAN)
- Wireless Network (WLAN)
12. What is the role of the network layer in TCP/IP?
The network layer in the TCP/IP protocol suite is responsible for logical addressing, routing, and packet forwarding across networks. It ensures that packets reach their destination by selecting the best path and handling network congestion.
13. What is the relationship between TCP/IP and the OSI model?
The TCP/IP protocol suite is a network protocol stack that predates the OSI model. While the OSI model has 7 layers, TCP/IP is often simplified to 4 layers: Network Interface, Internet, Transport, and Application. The TCP/IP model and the OSI model have similarities in terms of functionality but differ in the number and naming of layers.
14. How are IP addresses related to network layers?
IP addresses are associated with the Network Layer (Layer 3) in the OSI model.
15. Is WiFi considered a Layer 3 technology?
No, WiFi is not considered a Layer 3 technology. WiFi, also known as IEEE 802.11, operates at the Physical Layer (Layer 1) and the Data Link Layer (Layer 2) of the OSI model. It provides wireless connectivity for devices to access a network.
16. Which layer does DNS operate in?
DNS (Domain Name System) operates at the Application Layer (Layer 7) of the OSI model. It translates domain names into IP addresses and facilitates the resolution of domain names to their corresponding network addresses.
17. Is VPN considered a Layer 3 technology?
Yes, VPN (Virtual Private Network) is considered a Layer 3 technology. It operates at the Network Layer (Layer 3) of the OSI model. VPNs create secure connections over public networks by encapsulating and encrypting data packets, allowing remote users to access private networks securely.
18. What is the host layer in network architecture?
The host layer in network architecture refers to the Application Layer (Layer 7) of the OSI model. It represents the layer where applications and end-user processes directly interact with the network.
19. Can you provide an example of a network layer in action?
An example of a network layer in action is when you visit a website. The network layer ensures that your request is routed through various networks, from your device to the destination server. It handles addressing, packet forwarding, and routing decisions to ensure the data reaches its intended destination.
20. What are routers and their role in network layers?
Routers are network devices that operate at the Network Layer (Layer 3) of the OSI model. They facilitate the forwarding of data packets between networks, making routing decisions based on IP addresses. Routers play a crucial role in connecting networks and directing traffic efficiently.
By addressing these frequently asked questions, we aim to provide a better understanding of network layers and their significance in networking architecture. The interdependence of network layers ensures seamless communication, efficient data transmission, and reliable network infrastructure. We encourage readers to delve deeper into the world of network layers, explore advanced concepts, and stay up-to-date with the evolving field of networking.