While Linux is running our phones, friend requests, tweets, financial trades, ATMs and more, most of us don't know how it's actually built. This short video takes you inside the process by which the largest collaborative development project in the history of computing is organized. It is based on the annual report "Who Writes Linux," and it tells the compelling and motivational tale of how Linux evolved into a volunteer-driven phenomenon.
CSITechLK is a blog that covers technology topics such as mobile, software, hardware, and more. You will find tech talks, how-to guides, and latest information technology news on this blog. You will also learn from expert tutorials and reviews on various products and services. CSITechLK is your ultimate source for tech knowledge and updates.
27 July 2015
How Linux is Built
While Linux is running our phones, friend requests, tweets, financial trades, ATMs and more, most of us don't know how it's actually built. This short video takes you inside the process by which the largest collaborative development project in the history of computing is organized. It is based on the annual report "Who Writes Linux," and it tells the compelling and motivational tale of how Linux evolved into a volunteer-driven phenomenon.
02 July 2015
Social Media Security
Social Media
Privacy
Social media users frequently worry about securing their personal data. Possible risks include:
Overview
Social media platforms like Facebook, Twitter, Instagram, and LinkedIn are incredible tools that let you connect with, communicate with, and share with people all over the world. All of this power, though, also entails danger for you, your household, social circle, and employer. In this blog from CSITechLK, we explain what these dangers are and how to use these sites securely and safely.
Social media platforms like Facebook, Twitter, Instagram, and LinkedIn are incredible tools that let you connect with, communicate with, and share with people all over the world. All of this power, though, also entails danger for you, your household, social circle, and employer. In this blog from CSITechLK, we explain what these dangers are and how to use these sites securely and safely.
Privacy
Social media users frequently worry about securing their personal data. Possible risks include:
- Impacting Your Future: Only a few businesses regularly examine social media platforms. No matter how old they are, embarrassing or damning images or postings may keep you from being employed or promoted. In addition, a lot of colleges do comparable checks on applications from new students. Your privacy may not be protected by privacy settings since these organizations may invite you to "Like" or join their pages, and certain posts could be preserved across numerous websites.
- Attacks Against You: Cyber criminals can examine your posts and utilize them to get information about you or your company. For instance, they could use the information you offer to send you targeted emails (a practice known as spearfishing), try to figure out the answers to the questions you use to reset your online passwords, or phone a coworker while posing as you. Finding out where you live or work is one way that these assaults might have an impact on the outside world.
- Accidently Harming Your Employer: Any sensitive information you share about your corporation online might be used against you by criminals or rival businesses. Additionally, the reputation of your company might be harmed by your posts. Before publishing anything about your position, make sure to verify your company's regulations. Additionally, some of the social media postings you make could be watched.
Limiting what you post is the greatest kind of defense. Yes, privacy settings can offer some degree of security. But they frequently confuse you and alter without your awareness. For a variety of reasons, what you believed was private might abruptly become public. Your posts' privacy is also just as safe as the individuals you share them with. It is more probable that information you provide will become public the more friends or connections you have. You should consider whatever you upload as having the potential to become a permanent, public part of the Internet.
Finally, keep an eye out for what your pals are saying online. Ask them to remove whatever they publish if it makes you uncomfortable. Contact the social media platform and request that it take down the post on your behalf if they refuse or ignore you. Respect people' privacy while posting information about them.
Security
Here are some things to do in order to safeguard your social media accounts and online activity in addition to privacy issues:
Passphrases: http://www.securingthehuman.org/ouch/2015#april2015
Two-Step Verification: http://www.securingthehuman.org/ouch/2013#august2013
Securely Using Mobile Apps: http://www.securingthehuman.org/ouch/2015#january2015
Educating Kids on Cyber Safety: http://www.securingthehuman.org/ouch/2015#june2015
Facebook Security: https://www.facebook.com/safety
Here are some things to do in order to safeguard your social media accounts and online activity in addition to privacy issues:
- Login: Never share your passwords with anybody else and use strong, unique passwords to protect each of your accounts. Many social networking platforms also enable two-step verification for enhanced authentication. Always use these more powerful authentication techniques. Last but not least, avoid using your social networking account to access other websites; if it is compromised, all of your accounts are at risk.
- Privacy Settings: If you do utilize privacy settings, be careful to routinely check and test them. Privacy settings on social networking platforms are often changed, and mistakes are simple to make. Additionally, many applications and services allow you to geotag (or add your location information to) material that you share. If you want to protect the privacy of your whereabouts, make sure you often check these settings.
- Encryption: Online connections to social networking platforms are protected by HTTPS encryption. This is enabled by default on some websites (like Twitter and Google+), but you have to actively activate HTTPS on others. Verify the settings for your social network accounts and, whenever feasible, select HTTPS as the default connection.
- Email: Be wary of emails claiming to be from social media platforms. Cybercriminals may simply send faked attacks using them. The best approach to respond to such communications is to read and respond to any messages or notifications from the social networking website after logging in directly, maybe using a bookmark you've stored.
- Malicious Links/Scams: Be careful of any suspicious links or potential frauds that may be placed on social media platforms. Social media is used by bad guys to disseminate their own assaults. A message may not actually be from a buddy just because they submitted it; their account may have been hijacked. Call the person on their cell phone or get in touch with them in some other way to make sure the message is indeed from them if a family member or friend posts a strange message that you are unable to verify (for example, they were robbed and need money from you).
- Mobile Apps: The majority of social networking platforms provide mobile applications that let you access your internet accounts. Make sure your smartphone is secured with a strong password and that you download these mobile apps from a reputable website. When you lose your smartphone, if it is unlocked, anyone may use it to access your social media accounts and start posting as you.
Passphrases: http://www.securingthehuman.org/ouch/2015#april2015
Two-Step Verification: http://www.securingthehuman.org/ouch/2013#august2013
Securely Using Mobile Apps: http://www.securingthehuman.org/ouch/2015#january2015
Educating Kids on Cyber Safety: http://www.securingthehuman.org/ouch/2015#june2015
Facebook Security: https://www.facebook.com/safety
Subscribe to:
Posts (Atom)
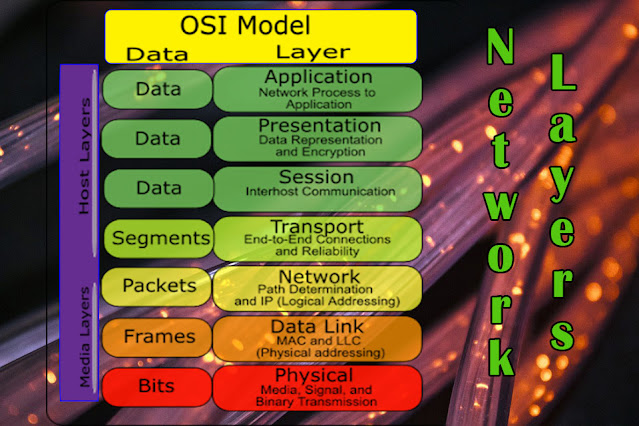
Understanding Network Layers: A Comprehensive Guide to Networking Architecture
Understanding Network Layers: A Comprehensive Guide to Networking Architecture Introduction Network layers serve as a fundamental framewor...